Threat Protection
Threat Protection
Our unique methodology combined with core offensive security-trained talent brings the best of both worlds, where you get the most comprehensive details of hidden gaps in your infrastructure as well as fast detection and mitigation of threats.

Threat Protection

Our unique methodology combined with core offensive security-trained talent brings the best of both worlds, where you get the most comprehensive details of hidden gaps in your infrastructure as well as fast detection and mitigation of threats.
Why is threat protection so important?
Threat protection service offerings
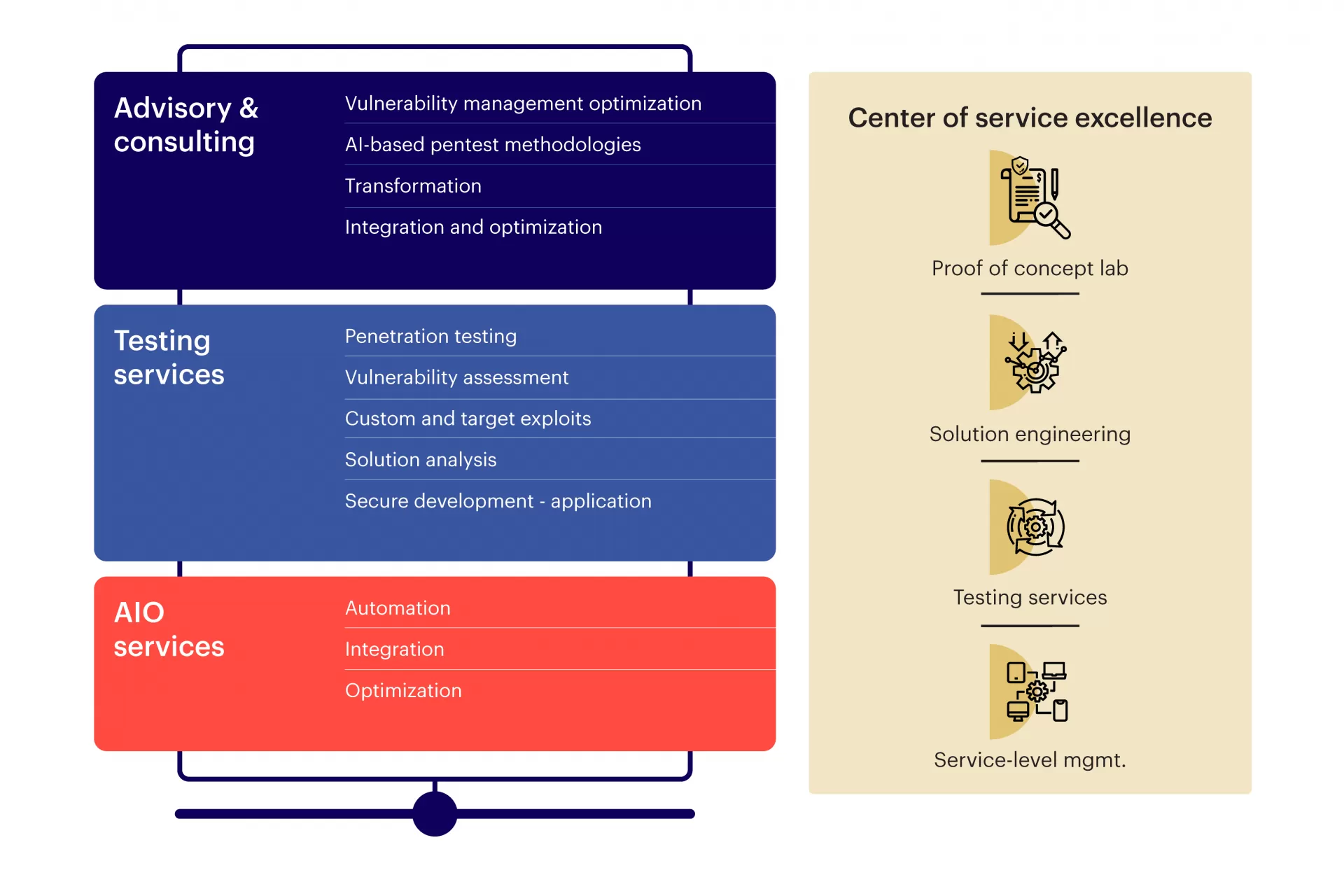
Our capabilities
Digital Security Offerings
Constantly evolving threats make businesses increasingly vulnerable to ransomware, viruses, and unauthorized access. Protect data, networks, and devices from malicious programs.
Our experience
Discover the stories that show how we’re transforming business through our expertise, digital transformation, and much more.
Explore other offerings

Intelligent Hybrid Infrastructure Services
Drive operational efficiency with human smarts backed by machine intelligence
Take me there
Digital Security
Protect data, networks, and devices from malicious programs and build better digital resilience
Take me there









