
Best Practices to shelter remote working culture by applying Zero Trust security
Read time: 4-5 Mins
During the pandemic we have seen a drastic rise in remote working, access on cloud services, BYOD devices and use of IOT devices. This is the reason we need a new way to secure Data, User Access and Network Infrastructure. Zero trust assume that until any activity is proven will be considered malicious.
Zero Trust is a secure infrastructure outline which works on the trust concept wherein the authentication, authorization and continuous validation is carried out by organization network architecture.
To accomplish the above three principles, Zero trust feature is essential with the following six components. Below shown is the Zero trust framework –
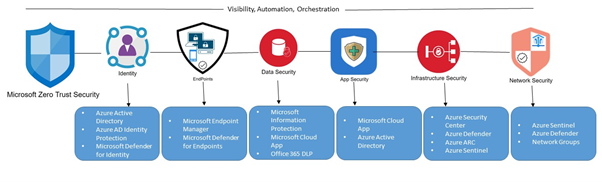
How does Zero Trust work?
Consider a user want to access the Emails/SharePoint from the secured cloud platform from trusted PC’s or Personal PC’s or Smart devices like Android or iOS or Surface. Zero trust work on the below model.
Until all 4-Steps are not verified, the user access is malicious until proven as per Microsoft slogan for Zero Trust Security “Never Trust, Always Verify”.
- 1st Step – Verify Identity:
- All user accounts set up for strong identity enforcement
- Strong identity enforced for Exchange
- Least – privileges User Rights.
- Eliminate Passwords – Biometric – based model
- 2nd Step – Verify Device Health:
- Device health required to access SharePoint, Exchange, Teams on iOS, Android and Windows.
- Usage data for application and services.
- Device management requirement to access corporate wireless network
- 3rd Step – Verify Access:
- Internet – Only for users
- Establish solutions for unmanaged devices
- Least – privilege access model
- Device health required for wired/Wireless corporate network
- 4th Step – Verify Services:
- Service health and proof of concept
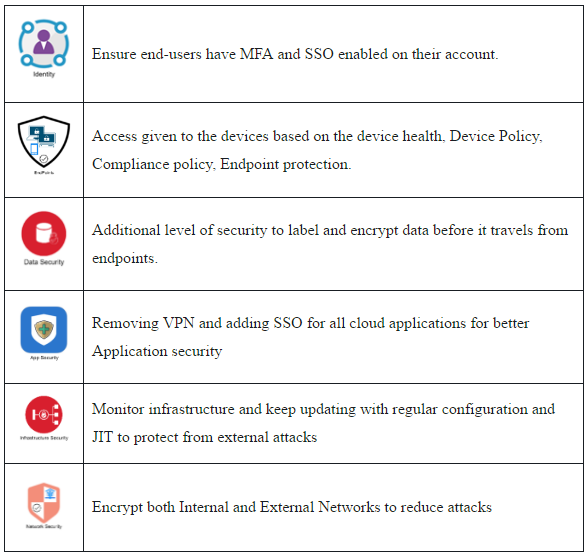
Developed model of Zero Trust framework –
Below framework shows the upgraded version of Zero trust model adapting to the new normal –
Benefits of Zero Trust –
There may be many different definitions for Zero Trust, the basic principle is that no user or device can gain network access without authenticating and being assigned application layer access rights. As a result, most zero trust implementations will provide:
- User to work from anywhere, anytime and on any device
- It will enable digital transformation with intelligent security for complex environment
- It will reduce the risk of lateral movement
The Role of Security in Zero Trust:
- Positively identifies all users who tried to access data and apps.
- Continuously authorize access based on risk and data sensitivity.
- Automatically adjust or block access in real-time to prevent attack damages.
- Protect and Monitor access to privileged accounts to prevent data breaches.
- Govern user to access to enforce least privileged model and reduce risk.
Key takeaway
- Zero trust is a security approach based on a mind-set that guides security investments, design decisions and operational security practices. It limits the trust placed in applications, services, identities and networks by treating them all as not secure and probably already compromised.
- Every access request is validated and investigated before approval
- Works on the principles of latest security technologies. (Azure Identity and Access Manager)
- Apply zero trust to every component of your organization
Zero trust systems can be intangible to the employees at the organization. They sign in, they use a strong security factor, and they are ready to go.
With a zero-trust model it’s easy to work from home and access all the same systems as the authentication and authorization aren’t limited to the location.
Switching to a zero-trust system will help the organization abridge their vulnerability and decrease security incidents, proactively put an end to phishing or spoofing-based attacks.
Zero trust is a path which organization takes depending upon the needs, resources. With its strong features of authentication, identity protection and access control, it provides a concrete foundation and gives a head start to the organization in the security space.



